_SERVICIOS_CIBER_7_PENTEST – English
PENETRATION TEST (PENTEST)
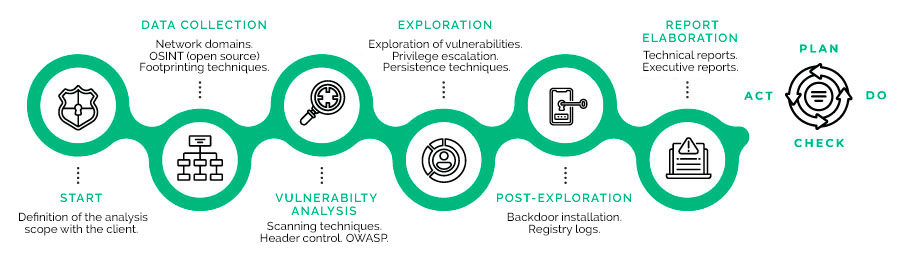
Unlike the Vulnerability Assessment, the PENTEST comprises the stages regarding the identified vulnerability exploitation and observes the real impact on the organization to define the associated risk.